Thursday, June 13, 2024 | Screenshot Tracking
It's challenging for employers to stop employees from using social media during work hours, but it seriously hurts productivity. Social media and other constant notifications distract employees and slow down their work.
Besides distractions, you also need to protect your employees from online threats and manage their work time to boost productivity. Is there a way to monitor this without directly watching them? Yes, there is! The stealth mode feature in employee monitoring software can help.
60% of companies plan to use employee monitoring software, including stealth tools, to track remote workers' productivity.
This blog will explore stealth mode, give examples, explain why employers should use it, and more.
Stealth employee monitoring software solutions fall into two categories: legitimate software for administrators to oversee device usage and malicious spyware that extracts data without the user's knowledge.
Employers can use non-malicious spy software to monitor employees on company-owned devices. Stealth or incognito monitoring is a proactive method where the monitoring system is invisible to employees. It helps alert managers and security personnel to illegal or suspicious activities without employees knowing they are being watched.
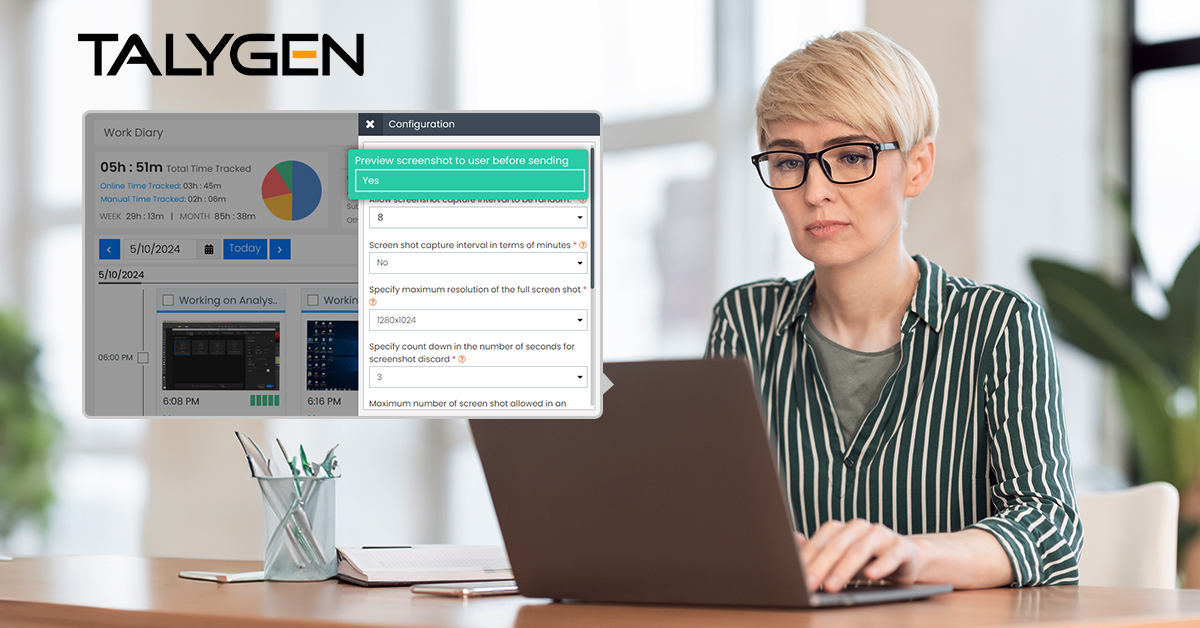
Software to monitor user activity, like Talygen, can be installed remotely via company servers to track employees' devices. With stealth features enabled, employees won't know that monitoring is happening. The main difference is that traditional monitoring involves employers and employees openly discussing monitoring practices. In contrast, stealth monitoring uses hidden software to monitor activity secretly.
The choice between stealth monitoring and transparent remote employee monitoring depends on the workplace, company culture, relevant laws, and the goals of employee tracking. Now that you know stealth monitoring, you must understand various examples of how it can be used.
Here are some common types of stealth monitoring software for computers:
These programs track internet activities by monitoring websites visited, search keywords, time spent online, and overall internet usage. They are often used to detect personal browsing during work hours.
Tools help managers and HR boost productivity, identify insider threats, gather evidence of misconduct, and prevent computer misuse. These tools often include features to alert designated personnel of suspicious or unethical activities.
User activity monitoring software solutions monitor how employees interact with their devices and the files they access. Companies use these tools to protect data by ensuring only authorized users access sensitive information.
Malicious programs secretly record device activities and steal data. Keystroke monitoring allows cyber thefts to spy on online conversations and steal passwords.
Here are some reasons employers choose to implement stealth monitoring in the workplace:

A productive team is crucial for any business. But how do you build such a team? The answer lies in understanding how employees spend their work hours. Silent activity tracking software helps achieve this by showing employees' focus on tasks, boosting personal growth and company success. Clear visibility of activities makes employees more accountable, significantly enhancing productivity and workflow.
Stealth monitoring solutions offer the best defense against data theft, whether unintentional or malicious. This software monitors suspicious online activities, reports them quickly, and takes necessary action, acting like digital security personnel for your business. It allows you to monitor who logs into your network and their activities, manage access to company resources, and spot intruders, ensuring your business stays secure.
Cyberloafing is when employees practice non-work activities more than productive activities while working. It includes spending excessive time endlessly scrolling through Facebook or playing games, which can be difficult to detect because these activities are not related to their office work.
Many employers worry about this when using stealth mode in employee computer monitoring software. Whether it's seen as an invasion of privacy depends on where and how the software is used.
If you use it for employee monitoring, you must follow the laws related to this practice. It's usually legal to monitor company devices during work hours.
Companies pay employees to perform specific duties and tasks, not to spend time on social media, watch videos, or chat with friends. While there are set working hours, employees can relax during official breaks like lunch.
Besides, in a standard work contract, most companies state that:
Moreover, using stealth computer monitoring software to track work time and attendance is expected, like using video cameras or electronic sensors. So, using it is legal and ethical.
Employers need to follow specific rules to comply with the law:
In some places, monitoring is legal only if mentioned in company policies and employees give written consent after signing their work agreement.
Many businesses must be careful because some employees access sensitive company information on computers, phones, and other devices. It's better to take precautions to prevent essential information leaks. Talygen’s Stealth computer monitoring software can help by efficiently tracking the time spent on apps and keystrokes without the employees' knowledge.
Now that you understand stealth mode, it's time to choose the best user activity monitoring software. Review the features and benefits of the stealth monitoring software to implement for achieving the company's goals and needs.